Next-Gen Security (via Cloud): Part 4 – Networks, Servers and Endpoints
Networks, Servers and Endpoints
Security monitoring and management of an organization’s network, server, and endpoints is critical to staying ahead of emerging threats that can adversely affect system components and the people and business processes that they support. The need to identify and protect the infrastructure against emerging threats has dramatically increased with the rise in organized and financially motivated network infiltrations (see more on APTs here).
The Security Governance, Risk Management, and Compliance model can provide guidance on the business implications of technology-based risks. In practice, the definition and management of technology-based threats, as well as the technical aspects of incident response, is either delegated to operational management and staff or outsourced to a service provider.
Recently, organizations have begun to leverage virtualization technology to support their goals of delivering services in less time and with greater agility. By building a structure of security controls within this environment, organizations can reap the goals of virtualization—such as improved physical resource utilization, improved hardware efficiency, and reduction of power costs, while gaining peace of mind that the virtual systems are secured with the same rigor as the physical systems (see Vmware’s VShield products). However, as many vendors who are servicing larger enterprises know, virtualization has far to go in the data center (larger organizations, on average, have virtualized 10% of the data center infrastructure…don’t get confused with % of organizations using virtualization). Also, to play the devils advocate further, analysts are saying that 60% of virtualized servers will be less secure than the physical servers they replace (see Gartner’s recent disclosure here).
From my perspective, the more important theme in securing networks, servers, and endpoints is to preemptively and proactively monitor the operation of the business and the IT infrastructure for threats and vulnerabilities….and do so with automated tools with integrated best-of-breed processes. And, as you would expect, my view is that this needs to be done through a SaaS offering which not only centralizes the tools, but captures policy that can be applied across the entire organization consistently.
SIEM SaaS = Step #1
Enter solutions like Loggly on the log management side….and then more interesting players who are advancing SIEM SaaS, like Sumo Logic. These are two IT SaaS categories which are well positioned to disrupt their respective markets consisting of a host of traditional players with on-premise solutions.
 With Loggly, you can collect logs from your servers and then quickly search them with an intuitive user interface. Others in this space include Logentries, Papertrail, Alert Logic with it’s log management SaaS service, and Splunk with a soon-to-be-released SaaS offering.
With Loggly, you can collect logs from your servers and then quickly search them with an intuitive user interface. Others in this space include Logentries, Papertrail, Alert Logic with it’s log management SaaS service, and Splunk with a soon-to-be-released SaaS offering.
Sumo Logic is an early-stage security startup backed by Greylock Partners. They are focused on delivering the next generation of IT and security management as a cloud-based service. Founded by principal developers from ArcSight (Christain Beedgen and Kumar Saurabh) and guided by product visionaries from SenSage (Bruno Kurtic). With Board members such as Shlomo Kramer (CEO of Imperva) and Aneel Bhusri (CEO of Workday), I can only guess that this team is building even more than SIEM as a Service.
As many of the Security 2.0 companies know, it will take more than leveraging scalable programming languages such as Scala or distributed database management solutions such as Cassandra to provide cloud-hosted security….especially when the incumbents are beginning to understand the value of using the cloud to deliver their services in a more efficient and cost-effective manner.
One direction we’re seeing is a tighter integration of log management, threat detection, and prevention solutions which all leverage a common data store. The approach is driven by the need to provide security staff with the means of more simply querying their logs across the entire enterprise, across network, server, and endpoints….and a simpler way to develop meaningful reports. It’s a natural evolution to see a combination of SIEM and IDPS (Intrusion Detection and Prevention Systems) into a single, integrated SaaS offering.
SIEM and IDPS in the Cloud = Step #2
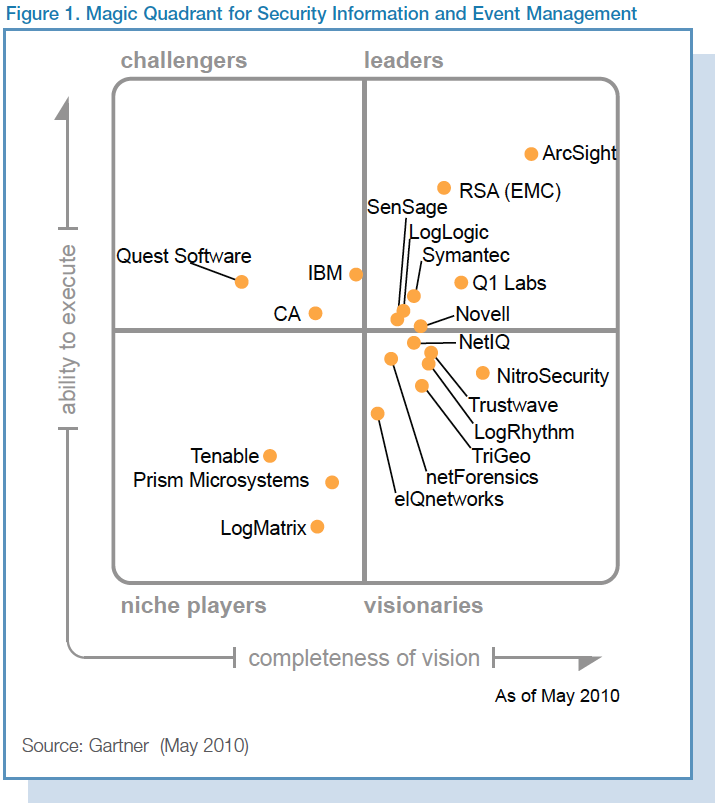
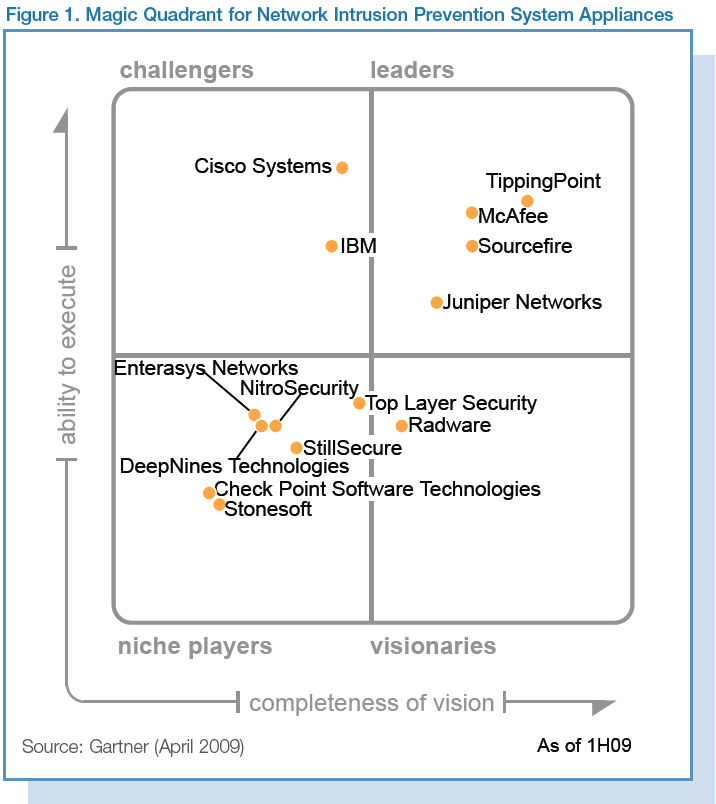
Lets look at the incumbents in these two adjacent spaces. Starting with SIEM.
ArcSight was clearly the thought leader, now apart of the HP family. Unfortunately, as part of HP we can probably “write them off” the list of innovators (we’re already seeing a lot of their talent leave the company).
The we turn to providers like Q1 Labs who have begun to broaden their offerings, like leveraging Layer 7 application flow data to detect inappropriate use of networked applications and protocols.
I suspect that most vendors like Q1 Labs are broadening their SIEM solutions by adding the ability to detect actions that attempt to compromise the confidentiality, integrity or availability of a resource. The systems naturally evolve into intrusion detection systems (IDS), designed to monitor all inbound and outbound network activity and identify any suspicious patterns that may indicate a network or system attack from someone attempting to break into or compromise a system.
Intrusion Detection can be performed manually or automatically. Manual intrusion detection might take place by simply examining log files or other evidence for signs of intrusions, including network traffic. A system that performs automated intrusion detection will be either host-based, if it monitors system calls or logs, or network-based if it monitors the flow of network packets, or both.
IPS, or intrusion prevention system, is the next level of security technology with its capability to provide security at all system levels from the operating system kernel to network data packets. It provides policies and rules for network traffic along with an IDS for alerting system or network administrators to suspicious traffic, and also allowing the administrator to provide the action upon being alerted.
Where IDS informs of a potential attack, an IPS makes attempts to stop it. Another huge leap over IDS, is that IPS has the capability of being able to prevent known intrusion signatures, and also some unknown attacks due to its database of generic attack behaviors.
TippingPoint, a thought leader in this space, was acquired by 3Com, who was then acquired by HP. Again, HP is making significant inroads into providing a turnkey suite of security services through acquisitions of best-in-class providers.
Then there are the more nimble players like Sourcefire, the provider of SNORT, Clam AV, and Razorback, who understands the power of open, with its many open source initiatives. Also with its recent acquisition of Immunet, a cloud-based AV solution, Sourcefile now has the domain expertise in SaaS.
So how do these technologies come together into a “next-gen security” cloud model (SaaS) that ultimately equates to simplified deployment, and management, at a lower expense?
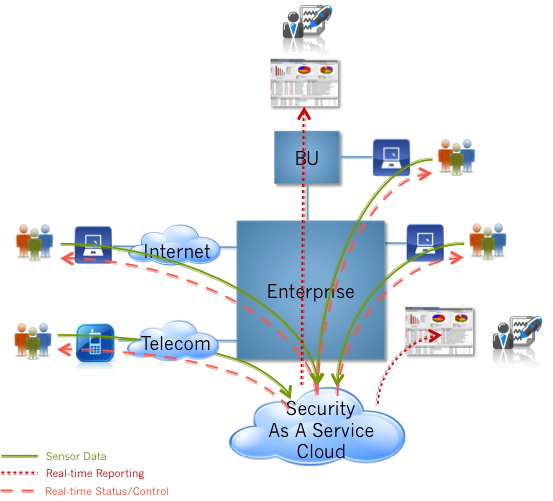
A cloud model for SIEM + IDPS
As shown in the above graphic, a next-generation security solution provided via cloud-services might be built with the following components:
- Data collectors: providing a means of integrating with existing SIEM systems, as well as being capable of capturing system (network, server, and endpoint) and application logs directly.
- Real-time data store: providing the means of processing unstructured data and allowing administrators to apply SQL-like queries against the data to determine trends, perform forensics, and predict the probability of future threats.
- Sophisticated Analytics: providing the ability to identify threats before signatures are created. These services would allow administrators to uncover botnet intrusion, for example, before zero-day events.
- Integrated Administration: providing configuration, deployment, and management across the entire organization from one centralized control center.
- Real-time Reporting: providing administrators (as well as users) real-time feedback. Next-gen reporting provides “facebook” like feedback to the enterprise, rather than traditional decision support-like reports which are run in batch every evening, or by the hour. Dashboards “come to life” with data that is aggregated from the enterprise in real-time.
- Discovery: providing administrators the ability to tailor their questions, processing network, server, and endpoint logs in manner that allows them to leverage their domain-expertise of the business. Human intervention is necessary to truly turn data into knowledge…taking raw event data and analyzing for trends, augments the automated algorithms developed by solution providers.
Via a SaaS model enterprises download agents which reside on networks, servers, and endpoints in a seamless and easy way, delivering on the power of the cloud such that there is “zero latency” in deployment to new devices as they are added to the enterprise. Examples of “IDPS as a Service” include offerings from Alert Logic (Threat Manager), and a few others including Metaflows.
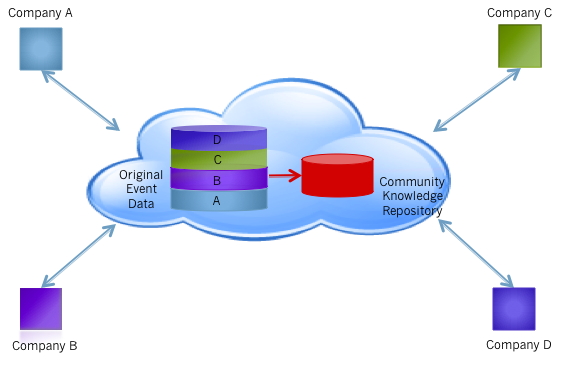
The Power Of The Community
When you collect information from your networks, servers, and endpoints across a broad number of enterprises, you gain the ability to pool that data into a single data warehouse which can be mined for community knowledge. This fact is not knew. However, what is novel is the ability to enable enterprises to leverage this community data themselves – providing a “security data as a service” for enterprise security staff to perform their own analysis. If Company A finds a new attack vector, they can query the community to see if they are seeing similar attack vectors, providing their metadata and analysis to others, in support of the greater good.
A Use Case
Looking at the service recently launched by Metaflows, a company providing IDPS as a Service, small and medium-sized enterprises can gain access to large enterprise-class security solutions at a fraction of the cost ($99/mth/sensor-CPU).
Rather than acquiring a CISCO ASA 5585 SPS-60 IPS for $150K, you instead download a number of network sensors for $99/month and install them on commodity servers already owned by the enterprise.
Envision sensors residing on all your physical and virtual network within the enterprise, monitoring the network as well as the servers and desktops on that network. In addition, any endpoints which are outside the enterprise firewall (e.g. telecommuting employees or mobile employees) can also install small, light-weight, cloud-enabled sensors which monitor their home and mobile networks.
Sensor data is captured and stored in real-time, allowing for immediate analysis and reporting. In addition, sophisticated analytics are constantly monitored for new attack vectors and, for example, uncovering botnets before they result in the loss of intellectual property.
The value of the Security As A Service
- Signature-less real-time network detection / prevention
- Real-time collection & analysis of information (from hosts, security devices, network devices, and endpoints)
- Real-time reporting of data & discovery of information
- Single system which requires no customization
- Light client-based agents (alleviating the need to burden users with constantly updating end devices with heavy apps)
- End device performance maintained (offloading heavy security processing software to the cloud)
- Uniform policy across the entire organization
- Centralized reporting platform for IT & execs
- Zero latency in deployment
- Pay-as-you-go cloud economics
More on the use of Cloud for securing your physical infrastructure to come….
Related Articles:
Next-Gen Security (via Cloud): Part 1 – Identity Management
Next-Gen Security (via Cloud): Part 2 – Data and Information
Next-Gen Security (via Cloud): Part 3 – Application and Process
Next-Gen Security (via Cloud): Part 5 – Physical Infrastructure




Awesome writing! It is awesome to see someone describe the future of computer security!
Now, I have to write a paper entitled: “It takes a Cloud to Secure a Cloud”. I will send you a copy of the article once it is written.
Livio.