Next-Gen Security (via Cloud): Part 3 – Application and Process
Application and Process
Enterprises need to proactively protect their business-critical applications from external and internal threats. Whether an application is internally focused, such as a customer relationship management (CRM) system delivered through a service-oriented architecture (SOA), or is an externally facing application, such as a new customer portal, clearly defined security policies and processes are critical to ensure that the application is enabling the business rather than introducing additional risk.
Identity management and authentication is no longer enough to protect against online web application attacks. Because of the authentication solutions put in place over the last few years like second factor and device ID, criminals have become much more sophisticated in how they perpetrate attacks against websites. To stay one step ahead of the criminals, it is critical that website malware and fraud detection systems perform more than authentication checks. Instead, the latest types of attacks, like Man in the Browser, require behavioral analysis of the website traffic.
Enter startups like Silver Tail Systems, Dasient, Incapsula, Zscaler, and others who focus on protecting your web applications.
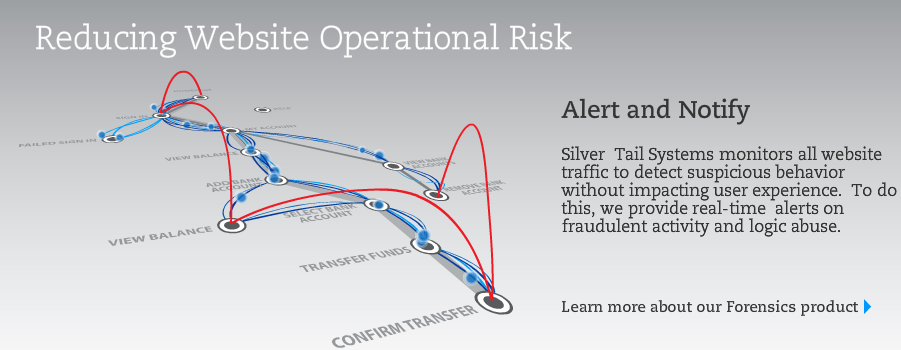
Silver Tail Systems’ Forensics solution provides behavioral analytics to detect emerging threats. In addition to its heuristic threat scoring capabilities, it also provides a business policy manager so fraud analysts can write business policies to be alerted to suspicious behavior. As typical with these new Security 2.0 offerings, Forensics provides a comprehensive point-and-click dashboard to make fraud investigations straightforward and efficient.
Forensics is installed by a system administrator by redirecting a span port on a switch to the Forensics data acquirer. This implementation takes on the order of hours – not months (no updates to html of the pages under protection). And Forensics can send alerts based on business policies to your current systems including case management systems, workflow systems, and SIEMs. Also, Forensics is available as either an on-premise installation or as Software as a Service (where SaaS is my preference, of course).
 Dasient takes a traditional approach to web application protection. Similar to classifying an event on the corporate website as “fraudulent”, the company provides a comprehensive offering to avoid your site from being blacklisted, defend against zero-day attacks, prevent visitors to your website from getting infected, and contain malicious code on your website.
Dasient takes a traditional approach to web application protection. Similar to classifying an event on the corporate website as “fraudulent”, the company provides a comprehensive offering to avoid your site from being blacklisted, defend against zero-day attacks, prevent visitors to your website from getting infected, and contain malicious code on your website.
The Dasient service detects any and all malware compromising a website through hourly, daily, and weekly scans using multiple scanning approaches: browser emulation, virtual machine emulation, and checking against blacklists and anti-virus engines.
Dasient identifies zero-day malware and malvertising with deep, precise scans using Dasient’s behavioral analysis technology.
Dasient scales infinitely to deliver a high-performance, low-cost architecture modeled on Google’s web-scale infrastructure.
The service delivers security intelligence based on massive amounts of telemetry data collected globally by monitoring millions of websites and dozens of ad networks for malware. The service effectively gathers the ‘wisdom of the masses‘ through its continuous web-wide monitoring, with results recorded in the Dasient malware infection library.
In addition to containing attacks automatically, it also provides tools for rapid removal of malware, so online businesses can get up and running quickly following a web malware infection.
What I love about hosted / SaaS services in the security space is the ability to leverage the ‘wisdom of the masses’, as Dasient describes it. You can begin to see the power of the infection library stats they pull together on a quarterly basis.
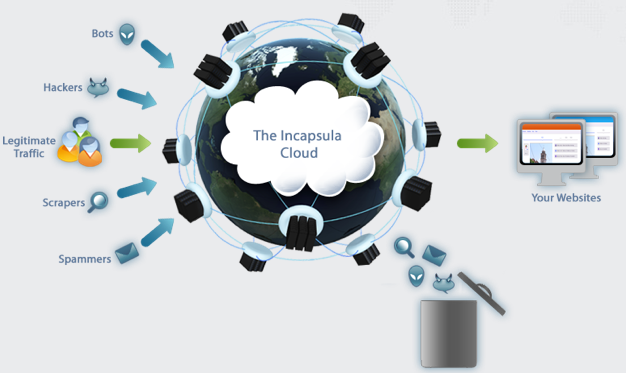
As the graphic above depicts, Incapsula offers security and performance software as a service. Once you put your website behind Incapsula, the company traffic is routed through the Incapsula global network of servers that inspect all incoming traffic, keeping hackers out while accelerating outgoing traffic.
Incapsula’s global network of servers will shield websites from hackers, spammers and other online threats and only permit legitimate traffic to reach it. At the core of the service is Incapsula’s Web Application Firewall (WAF) that constantly detects new attackers and threat vectors that emerge globally. Incapsula’s intelligence is shared across the entire network so that each website protected by the service receives the benefits of collaborative threat detection.
Incapsula makes your website faster by caching and optimizing its content and serving it directly from the internet’s backbone. Because it is a SaaS offering, it takes less than 5 minutes to add your website to Incapsula by making a simple change your domain’s DNS settings. There is no hardware or software to install or maintain and you can keep your current hosting provider. If you are ever unhappy you can turn Incapsula off as easily as you turned it on.
Zscaler has a similar offering and approach.
More on the use of Cloud for securing your network, server and endpoint; and physical infrastructure to come….
Related Articles:
Next-Gen Security (via Cloud): Part 1 – Identity Management
Next-Gen Security (via Cloud): Part 2 – Data and Information
Next-Gen Security (via Cloud): Part 4 – Networks, Servers and Endpoints
Next-Gen Security (via Cloud): Part 5 – Physical Infrastructure