Integrity of Things
The Beginning of Your Digital Identity
This somewhat dates me (as I just recently celebrated my half-century birthday)…I remember my Radio Shack TRS-80 color display computer with a dial-up modem connection to the CompuServe Information Service (CIS) in the early 1980’s. I received my TRS-80 under the Christmas tree when I was a teenager.
Back then the “Internet” was all about file transfers, bulletin boards, and email. This is also, arguably, the beginning of social networking when users could communicate with a central system where they could download games and post messages to each other.
AOL created its member-created communities (complete with searchable “Member Profiles,” in which users would list pertinent details about themselves). If you don’t agree that CompuServe created the first social network (aka community), then maybe you’ll agree that AOL led the social network era with its community-based website.
By the mid-1990s it was in full motion. Yahoo! had just launched, Amazon had just begun selling books, and the race to get a PC in every household was on (Windows Version 3.0 became the default for every new PC).
Then a transformational social media site launched, called Six Degrees in 1997. It was named after the ‘six degrees of separation’ theory. Six Degrees allowed users to create a profile and then friend other users. Six Degrees also allowed those who didn’t register as users to confirm friendships and connected quite a few people this way.
By the year 2000, around 100 million people had access to the internet, and it became quite common for people to be engaged socially online. Of course, then it was still looked at as an odd hobby at best (e.g. for geeks like me).
In 2002, social networking hit its stride with the launch of Friendster. Friendster used a degree of separation concept similar to that of the now-defunct SixDegrees.com, but refined it into a routine dubbed the “Circle of Friends” (yeap Google, you weren’t the first to try!), and promoted the idea that a rich online community can exist only between people who truly have common bonds. And it ensured there were plenty of ways to discover those bonds.
From there it’s history! Most people recall that “social” took off from there with networks like MySpace (2003), Linkedin (2003), Facebook (2004), and Twitter (2006).
From 2002 to 2016, we’ve seen 100M people in total across all social networks become over 2 billion users with 1.7 billion monthly active users on Facebook alone. The number of digital identities on the Internet has grown to almost half of the global population. As an end-consumer, you now have access to over 2 million digital applications just on your phone, and over 1 billion websites on the web….and social has powered much of this digital growth.
Social Networks Empower Digital Identities
Back in 2002, few knew that Larry Drebes was studying the huge potential of social networking while he was at Yahoo!. He had became a part of the Yahoo! team earlier when they acquired his company, Four11, which created the product RocketMail. Four11’s RocketMail became the basis of Yahoo! mail today.
Larry had envisioned a need where companies would need to manage the growing number of user digital identities. This led to his work as part of the founding team of OpenID, a protocol that allows users to be authenticated by co-operating websites (known as Relying Parties or RPs) using a third party identity authentication service. The thinking was that people on the Internet could register and login into their digital applications without having to have a separate identity and password for each. The OpenID protocol work led to Larry starting Janrain, and Larry realizing his vision. Janrain became the first to provide what is referred to as Social Login today, and that was only the beginning.
Identity Access and Management Explodes
Managing customer identities on both web and mobile applications is known by you and me through our daily experiences with traditional registration and login, social login, Single Sign-On (SSO), profile management (e.g. filling out your public information like your nick name, your city, schools attended, hobbies, etc) and preference management (e.g. what information that you want to opt into). It may seem simple, but the seamless consumer experience takes a lot of work under the covers by companies who are constantly enhancing your digital experiences.
Behind the scenes, your banks, retail stores, wireless carriers, hospitals, digital home product providers, and utility companies are all working with a group of Identity Access and Management (IAM) providers to offer a host of digital identity services that effectively automate identity services such as:
- User Provisioning
- Access Management
- Multi-Factor Authentication
- Single Sign-on
- Directory Services
- Password Management
- Governance & Compliance Management
Janrain may have been the first to create the category back in 2002, but now it’s one of many companies who have seen the potential in making consumer digital experiences simple and safe. Other companies in this space include:
All these companies have two fundamental things in common: 1) Identity and Access Management, of course, and 2) the End-User or Customer. These companies are better known for providing identity services to external end-customers as opposed to internal employees of global enterprise companies (employee identity and access management is used for legacy workforce applications and/or workforce to SaaS use-cases).
Vendors known for internal or more traditional employee-centric IAM include:
- Bitium
- Computer Associates
- Centrify
- Covisint
- Exostar
- Fischer International
- IBM / Lighthouse Security Group
- Ilantus
- Intermedia
- Microsoft
- Okta
- OneLogin
- Ping Identity
- RSA / Symplified
- SailPoint
- Salesforce
- Simeio Solutions
There is also a big difference between older solutions originally engineered for on-premise deployment (initially designed for physical servers in company data centers) versus native cloud engineered solutions. For example, companies like IBM, Oracle, Microsoft, and CA all initially addressed IAM through traditional software solutions whereas new entrants like Okta and OneLogin were born out of the public cloud generation.
Similarly, Janrain launched its native cloud services on Amazon in late 2005 right after the public cloud giant launched, whereas others in the customer identity and access management market established themselves as traditional software products.
Your Worst Nightmare – Digital Identity Theft
Javelin’s report, “2015 Identity Fraud: Protecting Vulnerable Populations“, found that fraudsters stole $16 billion from 12.7 million consumers in the U.S. ALONE in 2014. With a new identity fraud victim every two seconds, there continues to be a significant risk to consumers who embrace going digital.
Data breaches were a big headline in 2014 (per the Javelin report), and they had a significant impact on identity fraud – see eBay (145M customers), Target (110M customers), Anthem (80M customers), TalkTalk (4M customers), and Dropbox and Box. The study found that two-thirds of identity fraud victims in 2014 had previously received a data breach notification in the same year, with many indicating their wariness about shopping at merchants, including big box retailers.
The Yahoo! breach of over 500 million consumer identities announced this last month established 2016 as the “year of customer identity breaches” – it was the largest in history. Most consumers might not think there’s much in their Yahoo account that would be of use to hackers, which typically might only include their email and Yahoo password. However, those two bits of information offer multiple uses for ingenious hackers bent on extracting the maximum value from information, say experts.
According to a Gartner survey, 50% of users reuse their passwords across multiple platforms. So armed with an email address and Yahoo password, hackers might be able to gain access to multiple accounts. The technique is called “credential stuffing” and it’s become epidemic over the last year and a half, said Avivah Litan, a vice president and analyst at Gartner Research. “The bad guys get lists of user IDs and password and then test them, they run through them at all the sites they want to attack to see where they work,” she says.
Other credential theft results due to “holes” found in company’s identity implementations. Back in 2014, Target’s massive data breach in the U.S. that was tracked back to December 2013 involved personal information being stolen including credit/debit card details of close to 110 million individuals. According to Cowen Group’s (a financial services firm) note to investors, criminals were able to hack into Target due to a lack of security, which was later determined to be a direct result of under-investment. Target quickly embarked on technological changes that cost more than $100 million in addition to $61 million incurred in breach related expenses in Q4 fiscal 2013 alone! Since proactive investments into things like customer identity security is a CEO decision, Gregg Steinhafel was in the firing line. Shortly after the breach, the company stated that Steinhafel and board members had mutually decided that it was time for Target to continue under new leadership.
One particularly notorious identity theft story involves one Simon Bunce, an Englishman who subsequently lost his six-figure job and became alienated to friends and family. This all happened because his credit card was used to purchase and download child pornography. Bunce, an avid online shopper, claims to only have dealt with large retailers and secure sites. Nevertheless, he was swept up as part of a massive UK anti-predator police offensive called Operation Ore. He was arrested on charges of possessing, downloading, and intending to distribute indecent images of children. His home and work computers were confiscated, along with a range of storage devices and media. As you may already have gathered, though, Bunce was innocent of these crimes. Investigators later determined that his credit card details had been entered into a computer in Jakarta, Indonesia, and that he had actually been using the card at a South London restaurant at almost exactly the same moment. His credit card details had been taken from one of the many popular online shopping sites he frequented, as a result of a data breach. Although the situation was eventually resolved, Bunce said the damage had been done. “Being arrested and accused of what is probably one of the worst crimes known to man, losing my job, having my reputation run through the mud, it was a living nightmare,” said Brunce.
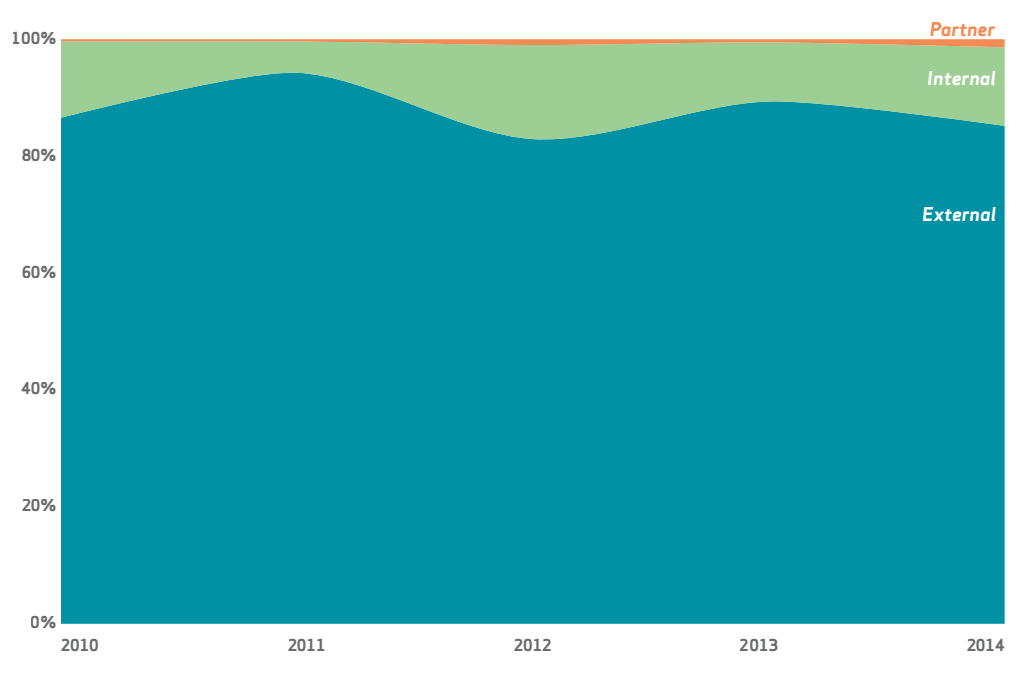
External Bad Actors using Your Credentials
You may have heard something differently, but the threat actors haven’t shifted much over the last five years. Based on the Verizon 2015 Data Breach Report, internal employees and partners (typically covered by enterprise identity access management vendors) is not where the real risk lies. It’s data breaches occurring from outside or external parties.
We find that most of the attacks make use of stolen credentials, “which is a story we’ve been telling since 1A.D”.
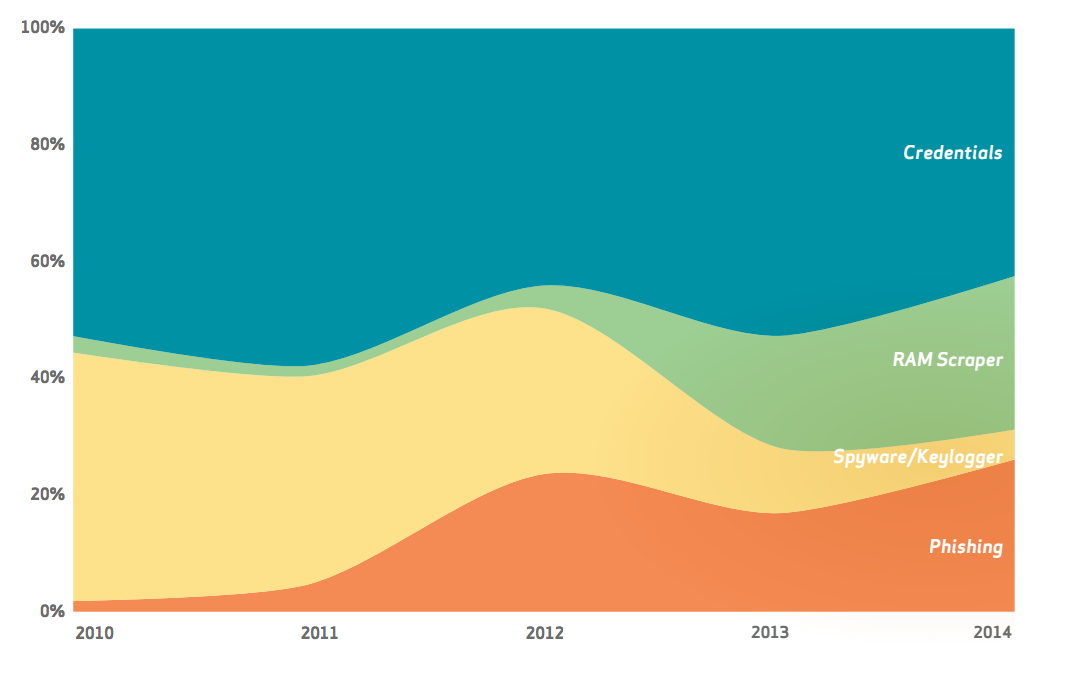
With attacks making use of stolen credentials, over 95% of these incidents involve harvesting credentials from customer devices, then logging into web applications with them.
Is it Identity or Integrity of Things?
I don’t know about you, but my digital identity is one of the most important things I own. As I’m renovating my home, I’m thinking of of the all the new digital applications I can leverage….from indoor and outdoor security cameras, digital door locks, IP-connected thermostat, digital water heater, IP-connected lights, and digital entertainment center. It’s one thing to have someone hack my credentials and force me to reset my social network password, but could they also take control of my digital home?
I want my digital world to have the utmost highest level of security, ensuring that the integrity of everything associated with me and my family. So, should I worry about my identity as it applies to the digital things in my life, or the integrity of the things associated with my identity? I do know that my digital identity will be even more important as I expand my digital world from web and mobile applications to consumer IoT devices.
When I drive home in my new Tesla S with built-in infotainment, I’m thinking about relaxing at home. I prefer my easy-listening station on Spotify around volume 5, with my home lights dimmed, and the temperature around 70 degrees Fahrenheit. That’s “Jim’s setting”. This is compared to my wife Annie’s preference for Indie Pop that would be up to eleven (if she could), with the lights bright, and the temperature around 60 degrees (I know what you’re thinking..but don’t say it!). That’s “Annie’s setting”.
We’re a “connected family”. I have two sons, Trevor and Devon, who both are heading into their teens and lets just say they don’t know what the word “analog” means.
Am I afraid of a rouge device adding itself to my network? Do I worry that someone can see my family lounging to Indi Pop through my indoor cameras? It’s definitely a growing issue, and a space that makes thousands of employees, or millions of consumers look like a small problem….trillions of internet connected things all exposed to bad actors?
I want that experience from my Tesla to digital home to be seamless…but also safe. How about you?