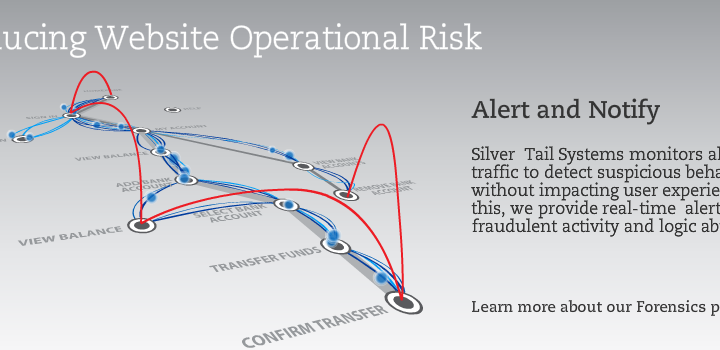
Application and Process Enterprises need to proactively protect their business-critical applications from external and internal
Data and Information When enterprises begin to use public cloud computing offerings, they receive the
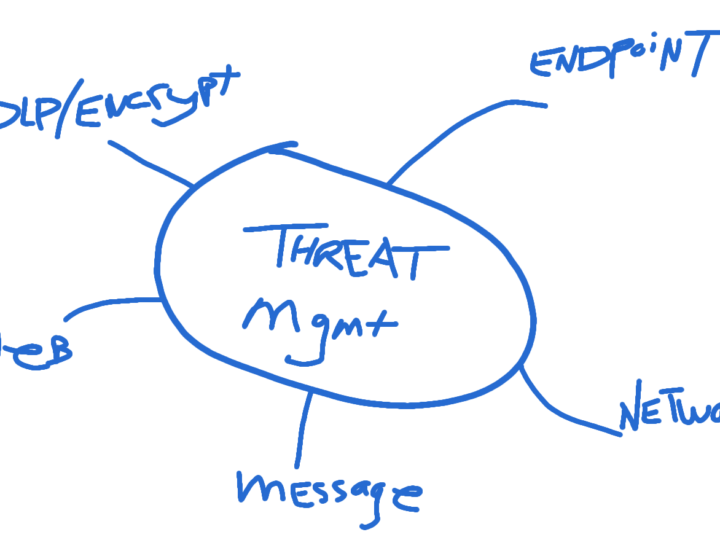
Security By Design Enterprises rely on computing systems and automation more than ever to detect
SecurID Can the enterprise spend enough money to truly secure itself? As anyone following security
The Game Development Lifecycle Generally speaking, a strong social game development team can produce a
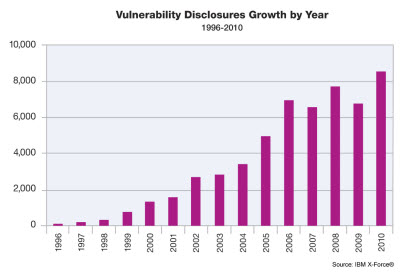
Security in 2010 When looking back last year, the actual number of breach incidents doubled
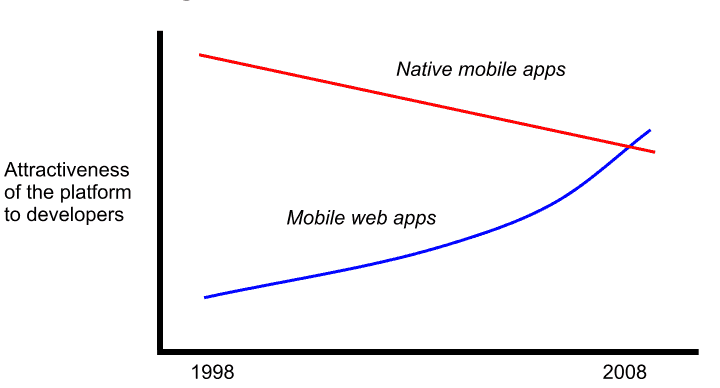
I spoke on a panel today covering “The Futures of Mobile Clouds” and one of
A recent colleague and good friend of mine recommended that I read “Who Killed Change?”
I was talking to a Wall Street firm that offers a suite of services that
Go To Market What is your go-to-market strategy? Are you a SaaS vendor who is