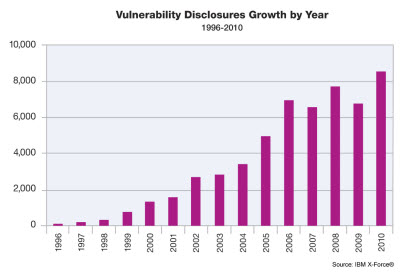
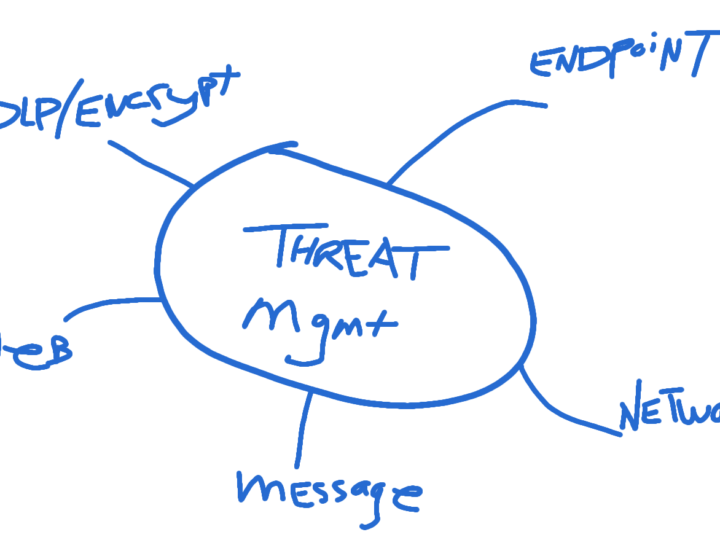
Category: Security
Or more appropriately described as Information Security, which means protecting information and information systems from unauthorized access, use, disclosure, disruption, modification, perusal, inspection, recording or destruction.
The terms information security, computer security and information assurance are frequently used interchangeably, sharing the common goals of protecting the confidentiality, integrity and availability of information.
My interests lie in the disruption of the security market by applying new technologies such as cloud computing. Of particular interest to me is the use of cloud to deploy “security as a service” which ultimately drives down cost, lightens the complexity of the client application, improves end-point performance, supports uniform policy, centralizes management, and delivers zero latency when it comes to deployment.